In today's digital age, ransomware attacks have become one of the most critical threats to businesses. These malicious programs lock your data, demanding hefty payments to release them. Unfortunately, many Nigerian businesses fall victim to ransomware due to insufficient cybersecurity measures. This article outlines practical, step-by-step solutions to help safeguard your business and minimize the risk of an attack.
Understanding Ransomware
Ransomware is a form of malware designed to encrypt files on a victim's device. Attackers demand a ransom, often paid in cryptocurrency, for the decryption key. Failure to pay within a specific time usually leads to the deletion of the data or higher ransom demands. Even though some businesses may think paying the ransom will solve the issue, it often doesn’t; your data may not be recovered, and attackers may come back.
Step-by-Step Solutions to Prevent a Ransomware Attack
1. Regular Data Backups
The first defense against ransomware is regular backups. If you have backups of your critical business data, ransomware won’t cripple your operations even if an attack happens. Backup data should be stored in multiple locations, including offline storage or cloud services that attackers cannot easily access.
How to Implement:
- Schedule automated backups daily or weekly.
- Use cloud services such as Google Cloud, AWS, or Azure.
- Test the restoration of data periodically to ensure the backups are functional.
2. Update Your Systems Regularly
Ransomware often exploits vulnerabilities in outdated software. Keeping your operating systems, applications, and antivirus software up-to-date is crucial.
How to Implement:
- Enable automatic updates for your systems.
- Assign an IT personnel or service to handle regular system maintenance.
- Frequently patch security vulnerabilities.
3. Invest in Robust Cybersecurity Software
An advanced firewall and antivirus solution can block ransomware before it infiltrates your system. Many cybersecurity software packages have ransomware protection, and some can identify unusual network activity.
How to Implement:
- Purchase a robust cybersecurity suite that includes firewall, antivirus, and ransomware protection.
- Monitor software updates and conduct regular security audits.
- Educate staff on recognizing fake emails or suspicious links.
4. Implement Multi-Factor Authentication (MFA)
To add an extra layer of security, enable Multi-Factor Authentication (MFA) for all user accounts in your business. MFA requires more than just a password—users must verify their identity with something they know, have, or are (such as a phone or fingerprint).
How to Implement:
- Use an MFA service such as Microsoft Authenticator or Google Authenticator.
- Mandate MFA for all employees and for critical access points in the system.
- Regularly update authentication policies and ensure that passwords are strong and not reused.
5. Train Employees on Cyber Hygiene
Human error is one of the primary reasons ransomware attacks succeed. Many attacks originate from phishing emails or weak passwords, and proper employee training can mitigate this risk.
How to Implement:
- Conduct regular cybersecurity awareness training.
- Teach employees how to recognize phishing scams and suspicious emails.
- Implement strict password policies and require employees to change them regularly.
6. Restrict User Access
Minimize the exposure of your system by restricting user access. Only provide employees with access to the data and applications necessary for their roles. The fewer people who have access to sensitive information, the smaller the chance of a breach.
How to Implement:
- Implement role-based access control (RBAC) for employees.
- Regularly review and update user privileges.
- Segment your network, so even if ransomware infiltrates one part, it can’t spread easily.
7. Create an Incident Response Plan
Even with preventive measures, no system is 100% foolproof. Preparing for the worst by creating an incident response plan can mitigate the damage. This plan outlines the steps your business will take if it experiences a ransomware attack, including who is responsible for what.
How to Implement:
- Draft a clear incident response plan with defined roles and timelines.
- Regularly test the plan with simulations or tabletop exercises.
- Have legal and IT teams on standby to minimize the damage of an attack.
8. Leverage Cloud Security
For businesses in Nigeria, leveraging cloud technology can enhance cybersecurity while cutting costs. Cloud services such as AWS and Microsoft Azure have built-in security protocols that prevent ransomware from affecting critical business operations.
How to Implement:
- Migrate sensitive operations to the cloud.
- Use cloud storage as an extra backup for critical files.
- Take advantage of the security features cloud platforms provide, including access management and encryption.
Real-Life Example: The Case of a N10 Million Business
One Nigerian entrepreneur learned the hard way how dangerous ransomware can be. After receiving a seemingly harmless email, his business files were locked, and the attackers demanded ?2 million to restore access. Fortunately, the company had a backup system in place, and the owner didn't have to pay a cent. Instead, they wiped their computers, restored the data from backups, and improved their cybersecurity, saving their business over ?10 million in potential losses.
Conclusion
Protecting your business from ransomware is not a one-time task but a continuous effort that involves updating systems, educating staff, and preparing for the worst. Whether you're a small business in Nigeria or a large multinational, taking these steps can save you from massive financial losses.
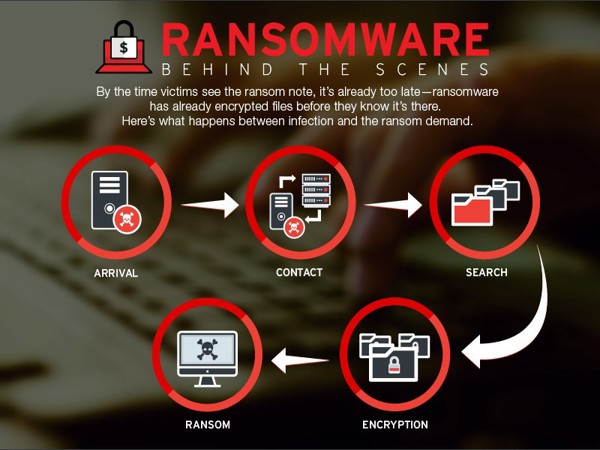
.jpg)







